Networking Single Sign On
February 1, 2024 at 12:48 AMNext Active Directory Integration provides support for pre-authentication with help of Kerberos or NTLM. It is only necessary that your webserver provides the current user principal in the environment variable X-REMOTE-USER, HTTP_X_REMOTE_USER or REMOTE_USER.
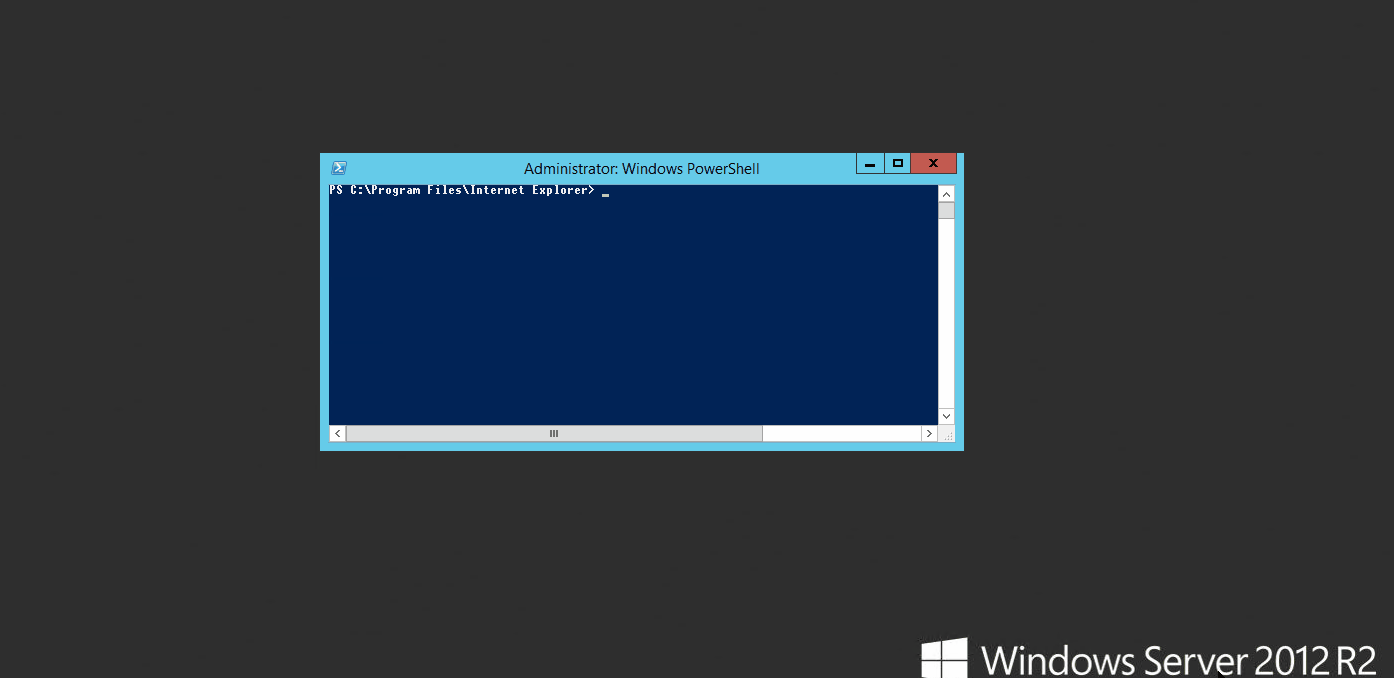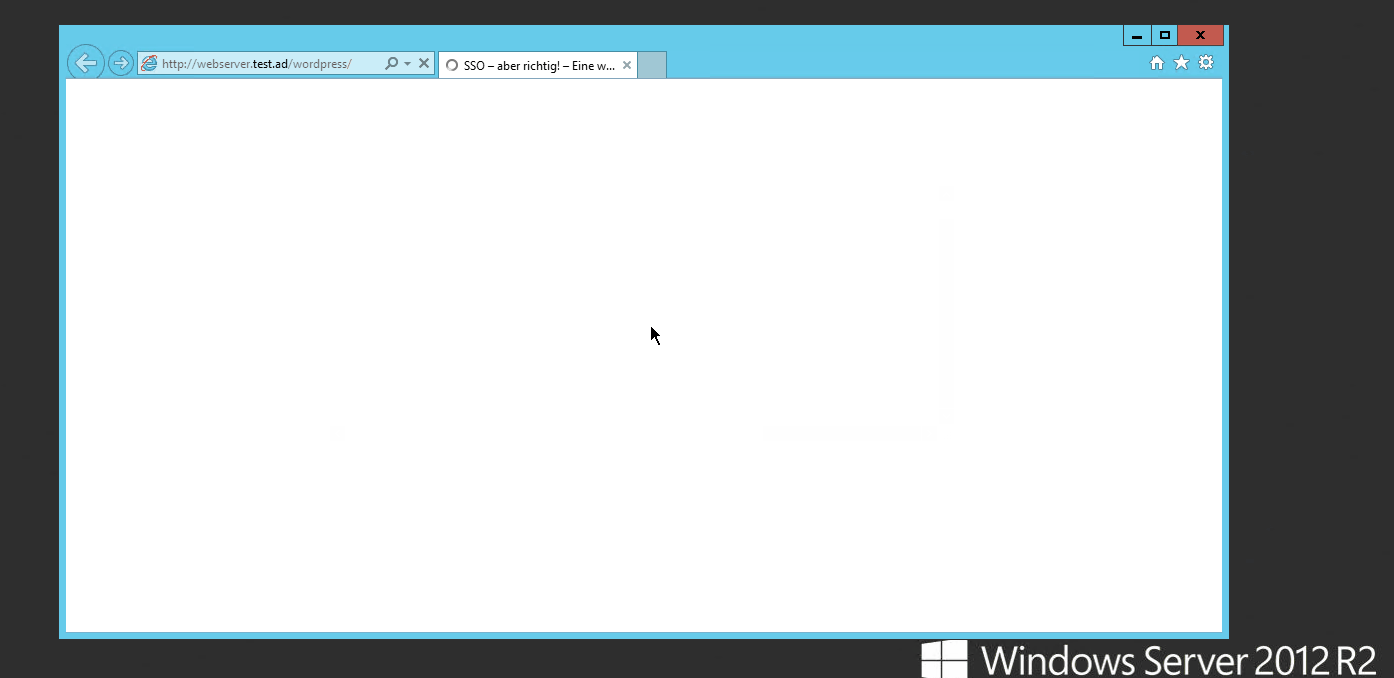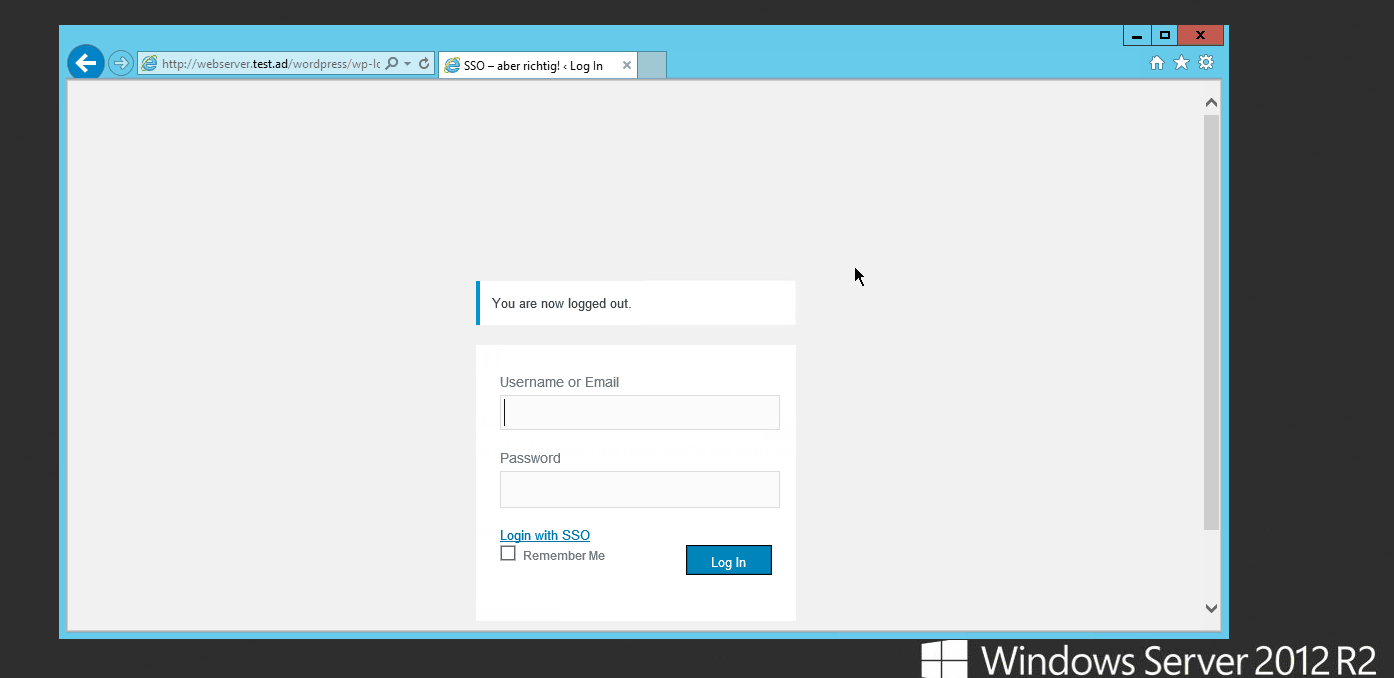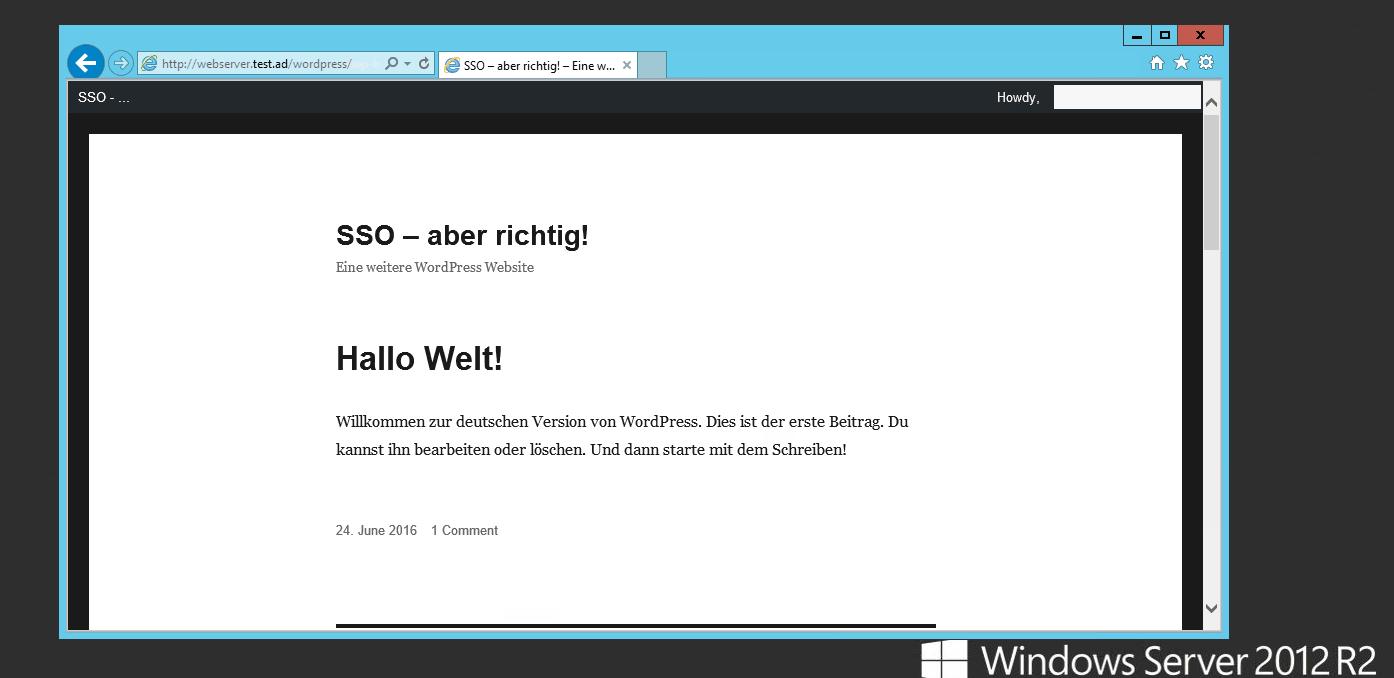
Implementation
When visiting your WordPress blog the first time, Next ADI checks for the environment variables provided by the webserver which could contain the username:
- If the username is provided as userPrincipalName@upnSuffix, Kerberos is used.
- If the username is provided as nETBIOSName\sAMAccountName, NTLM is used
- If a username is available, a dedicated service account is used to get the user’s data from Active Directory.
- With NADI 2.1.1 we also support claims based authentication. If the username is provided as claims|domain\username, NTLM is used.
Even if you have been previously authenticated by SSO, you can still log out and log in again without providing your password or log in with another username and password.
Notes
- Kerberos does only work for clients which got a Kerberos ticket from your domain controller.
- since 2.0.11 The user’s principal must be provided as sAMAccountName, userPrincipalName or nETBIOSname\sAMAccountName.
- In a multi domain environment your domain controller must provide the Kerberos principal as userPrincipalName to prevent duplicate accounts.
- Do not forget to configure the browser(s) you are using!