Configuration Security
February 1, 2024 at 12:48 AMTo keep everything secured you should be really attentive on this page. Please although read carefully the Security considerations section.
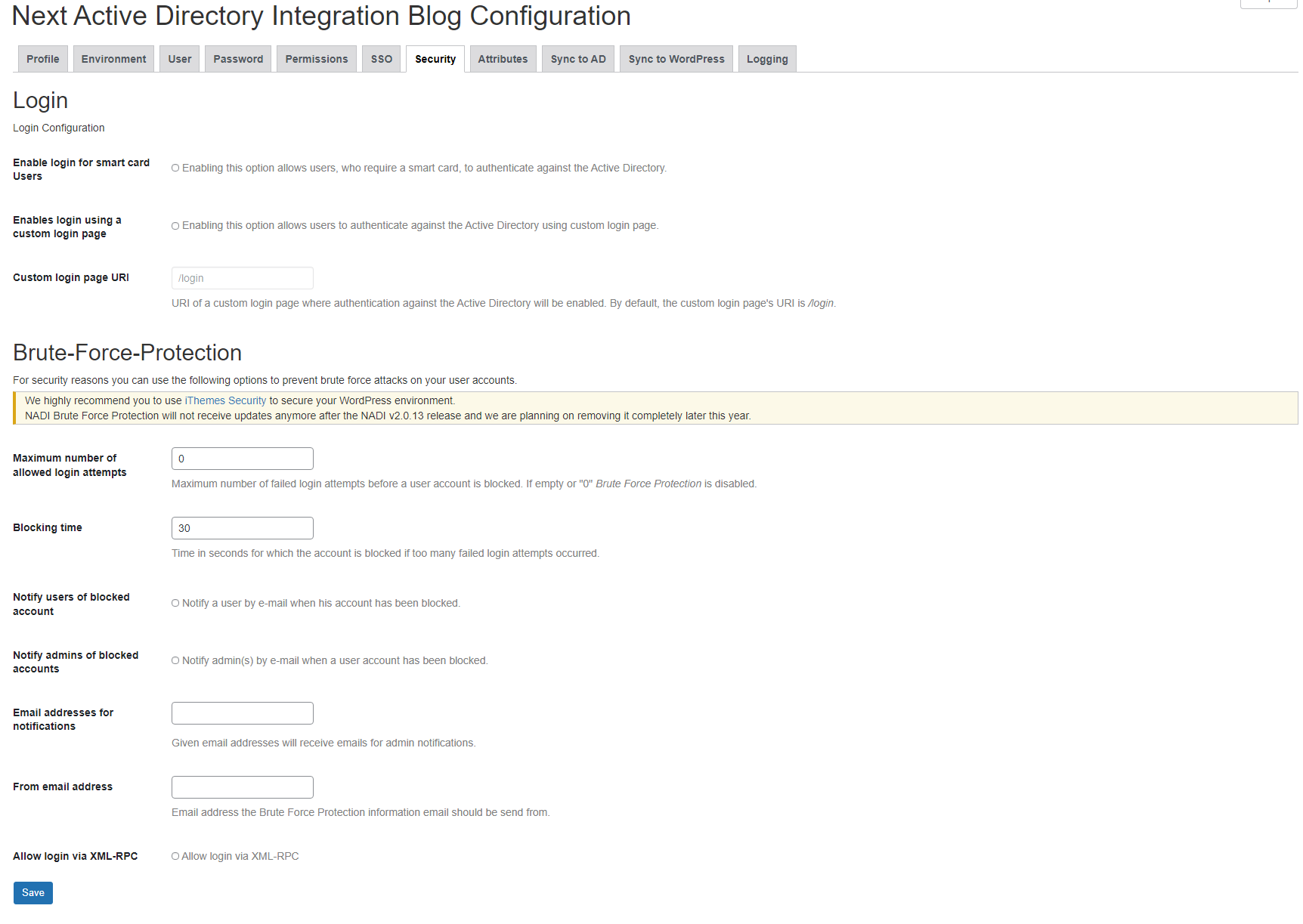
Login
Enable login for smart card Users
This option allows users that usually require a smart card to authenticate against the Active Directory to login into the WordPress environment. Users which were deactivated by NADI because they require a smart card will be activated at the next “Sync to WordPress”.
Enables login using a custom login page
If checked, NADI does also registers its hook when the URL /login is called. You have to make sure that this URL is mapped by WordPress.
Custom login page URI
since 2.3.2 If you have enabled the option Enables login using a custom login page, you can overwrite the default URI from /login to a custom URI of your choice. This might come in handy if you are using a plug-in like WPS Hide Login.
Brute Force Protection
The reason for that is that we can´t make it as secure as other existing security plugins.
That is why we started testing some Brute Force Protection plugins to see if they work in combination with NADI.
We highly recommend you to use iThemes Security to secure your WordPress environment.
NADI Brute Force Protection will not receive updates anymore after the NADI v2.0.13 release and we are planning on removing it completely later this year.
Maximum number of allowed login attempts
Enter the amount of tries a user has to login with his wrong username and/or password combination before he is blocked for a specific time period. If you want to disable the bruteforce protection just set this number to 0.
Blocking time
With help of this option you can set the time a user is being blocked after the amount of failed login attempts has been reached.
Notify users of blocked account
If enabled ADI notifies the user by email about the circumstance that his account has been blocked.
Notify admins of blocked account
Enabling this option will notify the admin(s) about blocked user accounts as well.
E-mail addresses for notifications
This option must be configured if you have enabled Notify admins of blocked account. It configures the email addresses of WordPress administrators. Multiple email addresses can be used by separating them by using a semicolon.
If the admin notification event is triggered and no admin email has been set, the email is forwarded to the blog administrator’s email address.
Example setting:
admin@company.com;me@mydomain.org
Allow login via XML-RPC
If enabled it is possible to authenticate by NADI imported users against the Active Directory using the XML-RPC interface. This means you can use a WordPress client like Open Live Writer to create posts on your WordPress site using NADI users. We also implemented this feature to secure that no one is able to use the WordPress XML-RPC interface to brute-force your Active Directory users. After the amount of failed login attempts has been reached, NADI will deny XML-RPC authentication request for the set amount of time. If you do not activate this option NADI will deny all XML-RPC authentication requests for NADI users.